Sunday, November 27, 2005
Interaction with *nix-based botnet channel
in my last post I quickly briefed on the idea of a possible mambo-based worm -- and these days, thats a very trivial task; since there are several templates of worms written with the task of exploiting several holes.
the other night I discovered an automated worm in the process of attacking my personal server. I grabbed the binary used in an attempted code inclusion, and discovered it was a basic kaiten.c binary. it had a default password of "bleh" from the original code, its servers pointed to undernet, and the channel "#uid0".
so, I joined the channel and noticed that there were several high profile machines up there, including ***.*** (which I've tried to contact but to no avail). the worms were going at full blast, for many machines a minute were logging into the channel. all kaiten. now usually when I find a kaiten channel, I tend to be evil and make the bots quit with a simple command. it's actually very trivial to do:
but the channel was in +m (moderated) mode.
I noticed a user on the channel, who had operator status, was running commands on a bot. I whois'd the bot and discovered it was an ***.*** machine. I contacted the user and asked him if he knew that trespassing onto the machine (in much simpler terminology) was illegal. I doubt he cared.
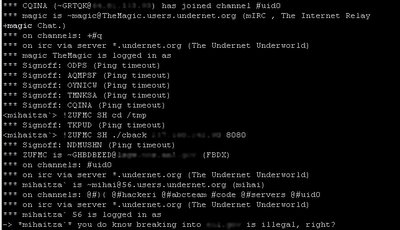
upon further questioning, he revealed the worm they used was running on C++, attacked xmlrpc, ekinboard, phpbb, and a few other web-based vulnerabilities (including mamboserver). he wouldn't show me the source, but I really didn't care anyway.
just another day in the neighborhood..
the other night I discovered an automated worm in the process of attacking my personal server. I grabbed the binary used in an attempted code inclusion, and discovered it was a basic kaiten.c binary. it had a default password of "bleh" from the original code, its servers pointed to undernet, and the channel "#uid0".
so, I joined the channel and noticed that there were several high profile machines up there, including ***.*** (which I've tried to contact but to no avail). the worms were going at full blast, for many machines a minute were logging into the channel. all kaiten. now usually when I find a kaiten channel, I tend to be evil and make the bots quit with a simple command. it's actually very trivial to do:
!* KILL
but the channel was in +m (moderated) mode.
I noticed a user on the channel, who had operator status, was running commands on a bot. I whois'd the bot and discovered it was an ***.*** machine. I contacted the user and asked him if he knew that trespassing onto the machine (in much simpler terminology) was illegal. I doubt he cared.

upon further questioning, he revealed the worm they used was running on C++, attacked xmlrpc, ekinboard, phpbb, and a few other web-based vulnerabilities (including mamboserver). he wouldn't show me the source, but I really didn't care anyway.
just another day in the neighborhood..